On Friday January 21, 2022 I received this email. I tweeted about it and it took off like crazy.
The email comes from a fortune-500 multi-billion dollar company that apparently might be using a product that contains my code, or maybe they have customers who do. Who knows?
My guess is that they do this for some compliance reasons and they “forgot” that their open source components are not automatically provided by “partners” they can just demand this information from.
I answered the email very briefly and said I will be happy to answer with details as soon as we have a support contract signed.
I think maybe this serves as a good example of the open source pyramid and users in the upper layers not at all thinking of how the lower layers are maintained. Building a house without a care about the ground the house stands on.
In my tweet and here in my blog post I redact the name of the company. I most probably have the right to tell you who they are, but I still prefer to not. (Especially if I manage to land a profitable business contract with them.) I suspect we can find this level of entitlement in many companies.
The level of ignorance and incompetence shown in this single email is mind-boggling.
While they don’t even specifically say which product they are using, no code I’ve ever been involved with or have my copyright use log4j and any rookie or better engineer could easily verify that.
In the picture version of the email I padded the name fields to better anonymize the sender, and in the text below I replaced them with NNNN.
(And yes, it is very curious that they send queries about log4j now, seemingly very late.)
Continue down for the reply.
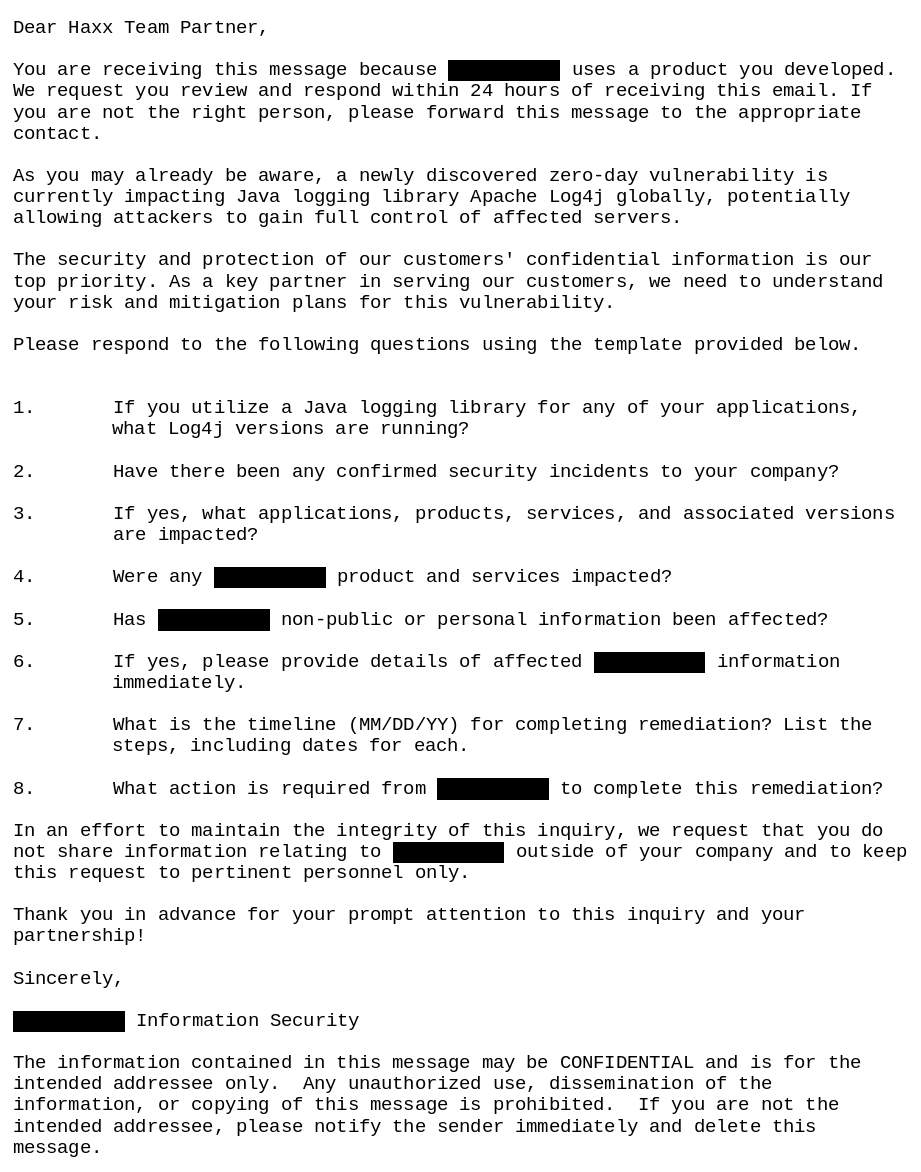
The email
Dear Haxx Team Partner, You are receiving this message because NNNN uses a product you developed. We request you review and respond within 24 hours of receiving this email. If you are not the right person, please forward this message to the appropriate contact. As you may already be aware, a newly discovered zero-day vulnerability is currently impacting Java logging library Apache Log4j globally, potentially allowing attackers to gain full control of affected servers. The security and protection of our customers' confidential information is our top priority. As a key partner in serving our customers, we need to understand your risk and mitigation plans for this vulnerability. Please respond to the following questions using the template provided below. 1. If you utilize a Java logging library for any of your application, what Log4j versions are running? 2. Have there been any confirmed security incidents to your company? 3. If yes, what applications, products, services, and associated versions are impacted? 4. Were any NNNN product and services impacted? 5. Has NNNN non-public or personal information been affected? 6. If yes, please provide details of affected information NNNN immediately. 7. What is the timeline (MM/DD/YY) for completing remediation? List the NNNN steps, including dates for each. 8. What action is required from NNNN to complete this remediation? In an effort to maintain the integrity of this inquiry, we request that you do not share information relating to NNNN outside of your company and to keep this request to pertinent personnel only. Thank you in advance for your prompt attention to this inquiry and your partnership! Sincerely, NNNN Information Security The information contained in this message may be CONFIDENTIAL and is for the intended addressee only. Any unauthorized use, dissemination of the information, or copying of this message is prohibited. If you are not the intended addressee, please notify the sender immediately and delete this message.
Their reply
On January 24th I received this response, from the same address and it quotes my reply so I know they got it fine.
Hi David, Thank you for your reply. Are you saying that we are not a customer of your organization? / [a first name]
My second reply
I replied again (22:29 CET on Jan 24) to this mail that identified me as “David”. Now there’s this great story about a David and some giant so I couldn’t help myself…
Hi Goliath, No, you have no established contract with me or anyone else at Haxx whom you addressed this email to, asking for a lot of information. You are not our customer, we are not your customer. Also, you didn't detail what product it was regarding. So, we can either establish such a relationship or you are free to search for answers to your questions yourself. I can only presume that you got our email address and contact information into your systems because we produce a lot of open source software that are used widely. Best wishes, Daniel
The image version of the initial email
The company
Update on February 9: The email came from MetLife.
Discussed
On Hackernews and Reddit

My reply would be way less tactful.
Something like.
To whom it may concern.
Allow me explain to you the nature of open source.
You used my free product, so my obligation to you ends at maybe patching it (maybe) if I decide its worth it to give a shit.
And your obligation begins at litterly everything else begining with the location of the check for update button in your package manager.
I’d do pretty much the same, albeit I’d probably spell “literally” correctly 😛
(Sorry. Grammar/Spelling pedant here.)
So, you are the David we are looking for.
You didn’t reply in 24 hours. Please expect the subpoena.
Just wait until they start accusing you of sabotaging their top tier security by delaying the required answer :,-D
Well, David opened the source code of this website, so he is hacking us
I doubt they forgot, I doubt they ever knew.
Something to consider.
@Jushua: I didn’t actually mean they forgot. They are clearly generally clueless about the whole situation…
Their incompetent management is probably just getting you to do their work for them for free.
To their defence (although I find this highly unlikely)
It may be that some “Top tier level/Top of the Brass” manager wanted an E-Mail confirmation and wouldn’t stop bothering the poor outsourced 3rd party support so the support wrote the email – full well knowing that this software is open source and when they got the replies (with the follow up) the poor 3rd party support would use those to roast the “Top” manager 😉
This is why open source licenses are extremely important. It Indemnifies you and puts owness back on the consumer (the enterprise in this case). Beyond that it’s the enterprise responsibility to ensure the governance is in place —side note have worked for several enterprises I can tell you most do not have a good oss governance process, it’s one of those unspoken magical things that happen in IT and only become a problem when it’s a problem.
Love it! I wait for next episode
I’d update my licensing to non-commercial use only for all future updates tbh.
More than likely this was just a templated email that went to dozens or hundreds of other software vendors/developers. If this was from a larger enterprise like some that I have worked for in the past, likely they asked the various IT support and development teams to compile a list of all the software/tools used in the enterprise and an email address for each one.
So…more likely just someone sending emails to vendors as requested in their project plan to mitigate the issue and checking off their box saying this vendor/developer was contacted. Etc. etc.
Most likely, the guy you were in contact with, doesn’t even know what your software is used for in their company.
This would have gone down like so in my company:
Company policy says, there needs to be a list of dependencies maintained, in case something goes wrong. So there is this (very much outdated and unmaintained) Excel sheet somewhere, that contains a list of dependencies. Some of them are closed-source and paid for, most others are open source.
The Excel sheet requires the devs to put in a point of contact for each dependency, so the dev that put your software on the list googled some kind of email address related to the software and put that in the list.
A wild security vulnerability appears.
Now the person in charge of that Excel sheet (who is not a dev and has no clue about how these dependencies are used, or what they even are) has to contact each of the owners of the dependencies and ask the same questions to them. They are not a dev, they don’t know anything about the dependencies, they probably don’t even know that Log4J is Java and curl is not.
Their purpose is not to actually do something useful here. They are doing that, so that they can tell their customers “We are doing all we can to fix that security vulnerability”. Most of the time, they are even contractually required to do so.
As much as I see why you see this as an issue for open source particularly, and I don’t disagree at all, this is almost as much of an issue inside companies.
I get this kind of stuff constantly from departments I have no idea who justified their existence. They ask stuff like this, often with even less technical or context understanding, no internal cost allocation (yes we have something like this), no justification to ask us anything, and certainly no understanding what we do. Then we spend lots of time to answer stupid questions, only for it to be filed away for ever.
No joke, I was once asked to fill out an Oracle DB details sheet of 3 pages of specific Oracle details, but we never used Oracle. Some software was running on Postgres, some on MySQL, some NoSQL, etc. and they said, well MySQL is from Oracle, isn’t it?
Evidently prepared by a legal team as qualified to do their jobs as the IT people who were presented wit the initial problem …
“We request you review and respond within 24 hours of receiving this email. If you are not the right person, please forward this message to the appropriate contact.”
“Any unauthorized use, dissemination of the information, or copying of this message is prohibited. If you are not the intended addressee, please notify the sender immediately and delete this message.”
I don’t understand. Are you supposed to immediately destroy this, or are you supposed to forward to the right person, while not disseminating a copy of the message.
Makes one want to “curl up” in a ball and roll around in circles ..
Personally, I would have sent them a blank response from a no no-reply email account