Back in December I got a desperate email from this person. A woman who said her Instagram had been hacked and since she found my contact info in the app she mailed me and asked for help. I of course replied and said that I have nothing to do with her being hacked but I also have nothing to do with Instagram other than that they use software I’ve written.
Today she writes back. Clearly not convinced I told the truth before, and now she strikes back with more “evidence” of my wrongdoings.
Dear Daniel,
I had emailed you a couple months ago about my “screen dumps” aka screenshots and asked for your help with restoring my Instagram account since it had been hacked, my photos changed, and your name was included in the coding. You claimed to have no involvement whatsoever in developing a third party app for Instagram and could not help me salvage my original Instagram photos, pre-hacked, despite Instagram serving as my Photography portfolio and my career is a Photographer.
Since you weren’t aware that your name was attached to Instagram related hacking code, I thought you might want to know, in case you weren’t already aware, that your name is also included in Spotify terms and conditions. I came across this information using my Spotify which has also been hacked into and would love your help hacking out of Spotify. Also, I have yet to figure out how to unhack the hackers from my Instagram so if you change your mind and want to restore my Instagram to its original form as well as help me secure my account from future privacy breaches, I’d be extremely grateful. As you know, changing my passwords did nothing to resolve the problem. Please keep in mind that Facebook owns Instagram and these are big companies that you likely don’t want to have a trail of evidence that you are a part of an Instagram and Spotify hacking ring. Also, Spotify is a major partner of Spotify so you are likely familiar with the coding for all of these illegally developed third party apps. I’d be grateful for your help fixing this error immediately.
Thank you,
[name redacted]
P.S. Please see attached screen dump for a screen shot of your contact info included in Spotify (or what more likely seems to be a hacked Spotify developed illegally by a third party).
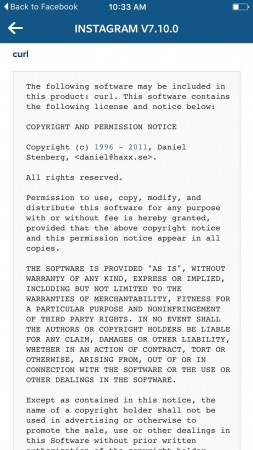
Here’s the Instagram screenshot she sent me in a previous email:
I’ve tried to respond with calm and clear reasonable logic and technical details on why she’s seeing my name there. That clearly failed. What do I try next?


You should tell her to ask anyone of her friends to show her your name is in their app installations too. Everyone has already been hacked by your code! 😉
point her to http://curl.haxx.se/docs/companies.html ?
These are known companies… 🙂
on second thought, maybe better not, she might get the wrong impression when she sees HAXX 🙂
I responded with an email suggesting that I probably also hacked all her friends’ phones and apps and also her TV, GPS, Bluray player, printer, car infotainment, tablets and more and that she better not use internet-connected devices at all to be really sure my name isn’t in any of the products she uses.
She obviously doesn’t understand free software at all, doesn’t know what curl or libcurl is, doesn’t know about code reuse and that this is just a copyright notice for your piece of the pie. You’re best off refusing to respond to all of her premises, and answer the question you wish she had asked which is “why is your name appearing in all of this software I use”?
Resistance is futile!
This might get you sued.
I would once again reiterate that you have nothing to do with their software. If she still doesn’t understand that you can’t help, I’d add her to my email blacklist.
Have you tried analogizing her actions to contacting Ford because she got hit by one of their cars?
It’s like contacting Skittles because there was a bag of skittles in the Ford that hit her.
It’s like contacting Skittles because there was a bag of skittles in _her_ car when she was hit by a Ford.
Just reply “Mess with the best, die like the rest.
Best regards Crash 0verride”
I’m going to guess that your domain being “haxx.se” doesn’t help your credibility with her.
I have found that explaining things like this in terms of cars help.
For example I would explain that programs are like cars. Ford makes cars but they don’t make all the parts they buy them from other manufacturers and put them together to make their car. You are the other manufacturer and just like manufacturer you put your name on the parts that you made.
Tell her that you wrote a software used by a lot of people around the world, free to use and very useful to software developers.
It can be used for good and for evil; some people used it for evil against her.
There is a chance she is dealing with a mental illness of some sort and is delusional. I know I had someone close to me who was mentally ill and was convinced that all her devices were hacked and developed all these unlikely theories. Just keep that in mind. Tread lightly and also if the person persists then cutting off communication with them might be the best option.
Hacked by some govermental agency und they also listen to their phonecalls?
^ Or maybe in terms of cameras, since she seems to have a career in photography. Anyway, drawing parallels is your best bet I guess.
I’d explain using an analogy. It might be a little patronising, but perhaps it will make more sense for her.
Just ignore it, she is the one with the problem, not you.
Point her to this blog and the comment section
Your domain name is Haxx. Average people think you’re a hacker. Obvious.
Hey! He is a hacker! 🙂
Tell her to tell whoever she wants. You are the author of a piece of software that thousands of programs use and if she contacts you again you will press charges of harassment. I am afraid this person might have an mental health issue.
Tell her the problem isn’t the Internet… It her localhost, which has been hacked… Software running on her own computer.
She’s likely not an admin, a user, so my advice: Re-Install your Windows / Linux.
Guys, she’s confused, not stupid or insane. Treat her like an intelligent person who is confused, but with respect otherwise, and watch the problem go away
Why do you put your email inside the terms?
For the lulz. I also do that, not that I have anything remotely as popular as libcurl with my email in it, but one can still hope…
Hackers are getting so formal these days. Including TOS, copyright, and licensing information.
silence, sweet silence.
you’re too kind.
Sqlite had similar problems:
https://github.com/mackyle/sqlite/blob/3cf493d/src/os.h#L52-L66
Direct her to
“THE SOFTWARE IS PROVIDED “AS IS”, WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.”
“Just like your name is attached to your photographs, my name is attached to my code. When someone uses one of your photos in a montage, they keep your name attached to it right? Likewise, when someone uses my code in their product, they keep my name on it.”
have you considered to point her to wikipedia?
https://en.wikipedia.org/wiki/Libcurl
You’ve been trolled. Congrats.
Firstly, great work asking for assistance from the community. I’d never guessed that people read these terms and conditions, and then tried to contact the people listed in there for assistance.
I’d suggest describing the situation by giving a non-technical real-world example of where this occurs elsewhere. For example, “my house got broken into, so I’m going to contact the brick manufacturer to ask for assistance in securing my house”. Or, “my car got stolen, so I’m going to contact the tyre manufacturer because they had something to do with the construction of the car”. If you can put it in real-world terms for her, it will help explain just how far away you are from being able to help her.
It was me
Here’s an analogy, related to her profession. You visit a hotel and when you return home you realize there’s something stolen. Then you visit the web page of the hotel and find her name on the photographs. So you call her to complain instead of the hotel manager.
That message made my head hurt.
I deal with people like this more often then I care to admit – if you want, drop me an e-mail privately with her contact info, and I’ll see if I can work my magic and get her set straight.
How about this?
“””
Hi,
Let me try to explain the situation a bit better.
I write a software component called libcurl. This software is used as a component in many many other software systems. An analogy is a pipe from the hardware store. I am supplying the “pipe” software that the Instagram corporation has chosen to plug into their system.
I am very sorry about the issues that you have had, but unfortunately, I do not control what other people do with my “pipe” software, and how they install their pipes, and what kind of system they make. Much like the pipe factory does not control what I do with the pipes I buy from the hardware store. The difference is that these software components tell you what kind of “pipe” (libcurl) they are using.
I regret to say, therefore, you will have to take up the issue with the pipe-buying companies: Instagram, Spotify, and Facebook.
Please accept my sympathy.
Regards,
Daniel Stenberg
“””
Very nicely written actually . Some people are challenging to get through to, but maybe this would work. I like the analogy.
Put her email in to https://haveibeenpwned.com/ and show her why her account was hacked
This is another example of why valuable information (in this case, photographs) should always be backed up locally as well as in the cloud. I back up my stuff with Backblaze and a local drive for PCs and Backblaze and Time Machine and Super Duper for Mac.
Have you considered forwarding her email to abuse@instagram.com with a short cover letter asking them to please help you by helping her?
Send her email to your spam engine’s training address? 😉
Anyone remembers this one?
http://www.theregister.co.uk/2006/03/24/tuttle_centos/
I wish you all the wisdom and patience handling this.
Legal action is not only possible, but likely, here, too.
Is she by any chance married or related to a guy from Tuttle, Oklahoma?
If yes, you should preemptively contact the FBI before she starts threatening to contact the FBI.
This made me giggle.
It confused me too, because the libcurl notice is displayed very prominently at the very bottom of the Third-Party Licenses page of the Libspotify SDK documentation of the Spotify Developer page. It would help if they removed the big popup that says, “Dear end user, you are expected to know or care about any of this.”
This doesn’t seem that absurd to me. It’s not as if this woman fell in a public library and sued some random author. Daniel’s name is in the software credits, as prescribed by the MIT, so the problem here is that in the FOSS world you sometimes might get a little more credit than you deserve. If this woman contacted Daniel to praise him for his effort, do you think he would mind so much? That being said, for her to assume that some random misfortune she experienced on two separate apps must be the result of a bug in a mutually occurring 3rd party library is textbook illusory correlation. That and not knowing how open source software works. Sure, you can try explaining all of that, or just leave it with, “I truly am sorry that your accounts were compromised. Even though my name appears in the software credits, this is solely due to copyright obligations. I do not develop the Instagram or Spotify apps and I’m not employed by Facebook or Spotify. Unfortunately you’ll have to forward this issue report to Facebook and Spotify; they will know how to handle it.”
As a car analogy, Toyota Hilux – ISIS relationship would be a good example in this situation! Does anyone accuse Toyota of supporting terrorism?
What do you do next? You write more good software and ignore the dumb people. Don’t waste your time replying to idiots – it’s not worth it, trust me.
Add her name to the copyright info? 🙂
I hate to point it out at this time, but I’m almost convinced she associated you with her issues because of the site URL, namely “haxx” part. I occasionally search for curl documentation and are subconsciously avoiding your site at first, thinking it is just some demoscene blog.
I’m sorry to hear about your trouble, man… I hope this lady understands how your name ended up in there eventually…
Relentless kindness and politeness and patience. People hate that.
Revert your name: https://github.com/mackyle/sqlite/blob/3cf493d4018042c70a4db733dd38f96896cd825f/src/os.h#L52 🙂
‘Also, Spotify is a major partner of Spotify’
Glad we got that cleared up.
This made my day! LOL
Tell the woman that you can’t help her recover the account.
Instruct the user to open a ticket with Facebook and Instagram.
If the user is a troll, problem solved. If the user is serious, Instagram will check if the user can be helped