I did a 25 minute talk yesterday in Swedish on the topic at the foss-sthlm meetup #5, and the slides from my presentation are available below.
Category Archives: Open Source
Open Source, Free Software, and similar
Fosdem 2011: my libcurl talk on video
Kai Engert was good enough to capture all the talks in the security devroom at Fosdem 2011, and while I’m seeding the full torrent I’ve made my own talk available as a direct download from here:
Fosdem 2011: security-room at 14:15 by Daniel Stenberg
The thing is about 107MB big, 640×480 resolution and is roughly 26 minutes playing time. WebM format.
libcurl, seven SSL libs and one SSH lib
I did a talk today at Fosdem with this title. The room only had 48 seats and it was completely packed with people standing everywhere it was possible around the seated guys.
The English slides from my talk are below. It was also recorded on video so I hope I’ll be able to post once it becomes available online
Foss-sthlm number five!
In the series of Free Software and Open Source talks and seminars we’ve been doing in the Foss-sthlm community, we are about to set off the fifth meetup on February 24, 2011 in Kista, Stockholm, Sweden. This time we will offer six talks by six different persons, all skilled and well educated within their respective topics.
The event will be held completely in Swedish, and the talks that are planned to get presented are as following:
- Foss in developing nations – Pernilla Näsfors
- Open Source Framework Agreements in the Swedish Government – Daniel Melin
- From telecommunications to computer networks – security for real-timecommunications over IP – Olle E Johansson
- Maintaining – how to manage your FOSS project – Daniel Stenberg (yes, that’s me)
- Peek in HTTP and HTTP traffic – Henrik Nordström
- Cease and desist, stories from threat mails received in the Rockbox project – Björn Stenberg
As usual, we do this admission free and our sponsor (CAG this time) will provide with something to eat and drink. After all the scheduled talks (around 20:00) we’ll continue the evening at a pub somewhere and discuss open source and free software over a beer or two.
See you there!
Rockbox on Maemo
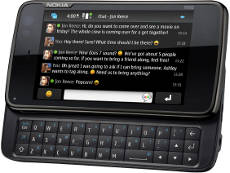 Thomas Jarosch has been quite busy and worked a lot on the Rockbox port for Maemo, it is the direct result of the previous work on making it possible to run Rockbox as an app on top of operating systems. It is still early and there are things missing, but it is approaching usable really fast it seems
Thomas Jarosch has been quite busy and worked a lot on the Rockbox port for Maemo, it is the direct result of the previous work on making it possible to run Rockbox as an app on top of operating systems. It is still early and there are things missing, but it is approaching usable really fast it seems
The work on the app for Android has also been progressing over time and even though it is still not available to download from the Android Market, the apk is updated regularly and pretty functional.
Going to FOSDEM 2011
 We’re going to FOSDEM again. This year we’ll ship over the entire company (all three of us) and we’ll join up with a few fellow Rockbox hackers and spend a weekend in Brussels among thousands of fellow free software and open source hackers.
We’re going to FOSDEM again. This year we’ll ship over the entire company (all three of us) and we’ll join up with a few fellow Rockbox hackers and spend a weekend in Brussels among thousands of fellow free software and open source hackers.
During this conference, 5-6 February, I’ve submitted a libcurl-related talk to the embedded-room that wasn’t accepted into the regular program, but I’ve agreed to still prepare it and I then might get a slot in case someone gets sick or something. A bit ungrateful as now I still have to prepare my slides for the talk but there’s a big risk that I’ve done it in vain! I’ve also submitted a suggestion for a second talk in the opensc/security room (also related to stuff in the curl project) but as of now (with but 16 days left) that schedule is yet to be announced so I don’t know if I’ll do a talk there or not.
So, I might do no talks. I might do two. I just don’t know. We’ll see.
If you’re a friend of mine and you’re going to FOSDEM this year, please let me know and we can meet and have a chat or whatever. I love getting faces to all the names, nicks and email addresses I otherwise only see of many people.
Update: My talk in the security room is titled “libcurl: Supporting seven SSL libraries and one SSH library” and will start at 14:15 on Saturday the 5th of February.
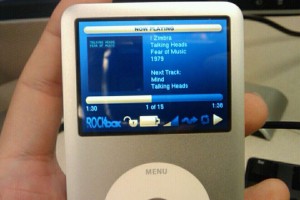
Rockbox seen on iPod Classic
After a very long time of work, a very very long time since these devices were introduced on the mp3 player market, the hard working guys from freemyipod.org have produced something on yet another device. This is the same group that previously was called linux4nano and worked so long and fiercely to get code running on the 2nd generation iPod Nano and the 4th generation iPod Nano.
At the end of December 2010, Michael “TheSeven” Sparmann announced that he was running custom code including music playback on the iPod Classic. The (sometimes) so called 6th generation.
Robert Menes spiced up the story today by showing us a live picture of a Classic device that now actually is running Rockbox:
Awesome work Michael, truly impressive. I hope a lot of Classic owners soon will be able to try out Rockbox for real. Rockbox is said to not yet be very stable or functional, so there’s a lot of room for more hackers and developers to join in and help us improve!
“Hacking me”
If you ever wonder how clever it was of me to make an FTP tool that used the default anonymous password curl_by_daniel@... once upon a time and you want to know why I changed that to ftp@example.com instead? Here’s a golden snippet to just absorb and enjoy:
Date: Thu, 23 Dec 2010 22:56:00
From: iHack3r <hidden>
To: info@[my company]
Subject: Hacking me
To the idiot named Daniel, Please stop brute force attacking my FTP client. I do not appreciate it, i have an anonymous account set up for the general public to access my files that i want them to access, QUIT trying to hack the admin because 1. DISABLED unless i am leaving to go somewhere without my computer 2: THE PASSWORD is random letters and numbers.
-iHack3r
The password was changed at Feb 13 2007 in curl version 7.16.2, but there are a surprisingly large amount of older curls still around out there…
Update: as the person responded again after having read this blog post and still didn’t get it, I felt the urge to speak up in even more clear terms:
I didn’t have anything to do with any “hacker attack” on any site. Not yours, and not anyone else’s. The fact that almost-my-email address appeared in your logs is because I wrote the FTP client. It is a general FTP client that is being used by a very very large amount of people all over the world. If I ever would attack a site, why on earth would I send along my real name or email address?
Byte ranges for FTP
In the IETF ftpext2 working group there have been some talks around clients’ and servers’ ability to do and support “ranged” file transfers, that is transferring only a piece of any given file. FTP supports the REST command and has done so since the dawn of man (RFC765 – June 1980), and using that command, a client can set the starting point for a transfer but there is no way to set the end point. HTTP has supported the Range: header since the first HTTP 1.1 spec back in January 1997, and that supports both a start and an end point. The HTTP header does in fact support multiple ranges within the same header, but let’s not overdo it here!
Currently, to avoid getting an entire file a client would simply close the data connection when it has got all the data it wants. The unfortunate reality is that some servers don’t notice clients doing this, so in order for this to work reliably a client also has to send ABOR, and after this command has been sent there is no way for the client to reliably figure out the state of the control connection so it has to get closed as well (which is crap in case more files are to be transferred to or from the same host). It primarily becomes unreliable because when ABOR is sent, the client gets one or two responses back due to a race condition between the closing and the actual end of transfer etc, and it isn’t possible to tell exactly how to continue.
A solution for the future is being worked on. I’ve joined up the effort to write a spec that will suggest a new FTP command that sets the end point for a transfer in the same vein REST sets the start point. For the moment, we’ve named our suggested command RANG (as short for range). “We” in this context means Tatsuhiro Tsujikawa, Anthony Bryan and myself but we of course hope to get further valuable feedback by the great ftpext2 people.
There already are use cases that want range request for FTP. The people behind metalinks for example want to download the same file from many servers, and then it makes sense to be able to download little pieces from different sources.
The people who found the libcurl bugs I linked to above use libcurl as part of the Fedora/Redhat installer Anaconda, and if I understand things right they use this feature to just get the beginning of some files to check them out and avoid having to download the full file before it knows it truly wants it. Thus it saves lots of bandwidth.
In short, the use-cases for ranged FTP retrievals are quite likely pretty much the same ones as they are for HTTP!
The first RANG draft is now available.
Add latency to localhost
Pádraig Brady taught me a great trick in a comment to a previous blog post and it was so neat I feel a need to highlight it further as it also makes it easier for me to find it again later!
To simulate a far away server, add RTT time to the localhost device. For example if we add 100 milliseconds (which then makes 200ms ping time to localhost):
tc qdisc add dev lo root handle 1:0 netem delay 100msec
Restore it back to normal again with:
tc qdisc del dev lo root
In addition, add a random packet loss. 500ms latency with 2.5% packet loss:
tc qdisc add dev lo root handle 1:0 netem delay 250msec loss 2.5%