Since I’m doing my share of both FTP and HTTP hacking in the curl project, I quite often see and sometimes get the questions about what the actual differences are between FTP and HTTP, which is the “best” and isn’t it so that … is the faster one?
FTP vs HTTP is my attempt at a write-up covering most differences to users of the protocols without going into too technical details. If you find flaws or have additional info you think should be included, please let me know!
The document includes comparisons between the protocols in these areas:
- Age
- Upload
- ASCII/binary
- Headers
- Pipelining
- FTP Command/Response
- Two Connections
- Active and Passive
- Firewalls
- Encrypted Control Connections
- Authentications
- Download
- Ranges/resume
- Persistent Connections
- Chunked Encoding
- Compression
- FXP
- IPv6
- Name based virtual hosting
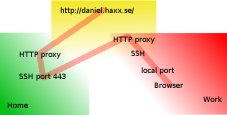
- Proxy Support
- Transfer Speed
With your help it could become a good resource to point curious minds to in the future…