Android, the software environment, has gotten a lot of press, popularity and interest from all over lately. People on the streets know there’s something called Android, companies know people know and so on. Everyone (well apart from a few competitors perhaps) likes Android it seems.
Being an embedded guy I like keeping an eye on the embedded world and Android being pretty embedded this at least tangents my universe. What is Android anyway? android.com says Android is “an open-source software stack for mobile devices, and a corresponding open-source project led by Google“. Not very specific, is it?
Android on different devices
You can already find Android on mobile phones, media players, tablets, TVs and more. Very soon we’ll see it in car infotainment equipment, GPSes and all sorts of things that have displays. Clearly Android is not only for mobile phones and not even necessarily for mobile things. TVs often aren’t that mobile… And not touchscreen either.
Android with tweaks
The fact that there hardly are two Android installs completely alike is frequently debated. Lots of manufacturers patch and change the look and feel of Android to differentiate. Android is not associated with any particular look or feel quite clearly.

Android with binary drivers
Almost all Android installations you get on the Android phones and devices today have a fair amount of closed, proprietary drivers. It means that even if the companies provide the source code for all the free parts in time (which they sometimes have a hard time to do it seems), there are still parts that you don’t get to see the code for. So getting a complete Android installation from source to run on your newly purchased Android device can be a challenge. Also, it shows that Android can consist of an unspecified amount of extra proprietary pieces that don’t disqualify it from being Android.
Android without apps
I have friends who work on devices where the customer has request them to run Android, although they don’t have any ability to run 3rd party apps. Android is then only there for the original developers writing specific code for that device. Potential buyers of that device won’t get any particular Android benefits that they might be used to from their mobile phones running Android, as the device is completely closed in all practical aspects.
Android without market
Devices that don’t meet Google’s demands and don’t get to be “Google certified” don’t get to install the google market app etc, but at least a company who wants to can then in fact install their own market app or offer another way for customers to get new apps. The concept of getting and installing apps aren’t bound to the market app being there. In fact, I’ve always been expecting that some other companies or parties would come along and provide an alternative app that would offer apps even to non-google-branded devices but obviously nobody has yet stepped up to provide that in any significant way.
Android without Java
I listened to a talk at an embedded conference recently where the person did a 40 minute talk on why we should use Android on our embedded systems. He argued that Android was (in this context) primarily good for companies because it avoids GPL and LGPL to a large extent. He talked about using “Android” in embedded devices and cutting out everything that is java, basically only leaving the Linux kernel and the BSD licensed bionic libc implementation. Of course, bionic may now also provide features to the rest of the system that glibc and uClibc do not, they being designed as more generic libcs.
Personally, I would never call anything shipped without the Java goo layers to be Android. But since it was suggested, I decided to play with the idea that a platform can be “Android” even without Java…

That particular license-avoiding argument of course was based on what I consider is a misunderstanding. While yes, lots of companies have problems with or are downright scared of the GPL and LGPL licences, but I’ve yet to meet a company who have any particular concerns about the licensing of the libc. I regularly meet and discuss with companies who have thoughts and worries about GPL in the kernel and they certainly often don’t like *GPL in regular libraries that they linked with in their applications. I have yet to find a customer who is worried about the glibc or uClibc licenses.
In fact, most embedded Linux customers also happily run busybox that is GPL although we know from history that many companies do that in violation with the license rules, only to get the lawyers running after them.

Android is what?
As far as I know Android is a trademark of some sorts, and so is Linux. If you can run an “Android” that is just a kernel and libc (and I’m not saying this is true beyond doubt because I’ve not heard anyone authoritative say this), isn’t that then basically a very very small difference to any normal vanilla embedded Linux?
The latter examples above are even without any kind of graphical UI or user-visible interface, meaning that particular form of “Android” can just as well run your microwave or your wifi router.
Without the cruft can we change the kernel?
The Android team decided that a bunch of changes to the Linux kernel are necessary.to make Android. The changes have been debated back and forth, some of them were merged into mainline Linux only to later get backed out again while the greater part of them never even got that far. You cannot run a full-fledged Android system on a vanilla kernel: you need the features the patches introduce.
If we’re not running all the java stuff do we still need those kernel patches? Is bionic made to assume one or more of them? That brings me to my next stepping stone along this path:
Without the patches can we change libc?
If we don’t run the java layers, do we really have to run the bionic libc? Surely the Android kernel allows another libc and if we use another libc we don’t need the Android kernel patches – unless we think they provide functionality and features that really improve our device.
Android is the new Linux?
Android as a name to describe something really already is just as drained as Linux. All these Android devices are just as much Linux devices and just as a “linux device” doesn’t really tell anything about what it is actually more than what kernel it runs, neither does it seem “Android device” will mean in the long run or perhaps already.
Android however has reached some brand recognition already among mortals. I think Android is perceived as something more positive in the minds of the consumer electronic consumers than Linux is. Linux is that OS that nobody uses on their desktops, Android is that cool phone thing.
I will not be the slightest surprised if we start to see more traditional Linux systems call themselves Android in the future. Some of them possibly without changing a single line of code. Linux one day, Android the next. Who can tell the difference anyway? Is there a difference?

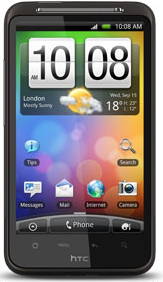

 I’ve not yet used the HD enough in a similar way that I used the Magic to be able to judge how the battery time compares. The Magic’s 1340 mAh battery spec against the HD’s 1230 mAh doesn’t really say much. The HD battery is also smaller physically.
I’ve not yet used the HD enough in a similar way that I used the Magic to be able to judge how the battery time compares. The Magic’s 1340 mAh battery spec against the HD’s 1230 mAh doesn’t really say much. The HD battery is also smaller physically.







 I did my day as part of a three-day course, and I got to do the easy part: user-space development. My day covered the topics of: Embedded Linux development introduction, how to build, autobuilding, how to run, git basics, debugging, profiling and finally some brief words on testing.
I did my day as part of a three-day course, and I got to do the easy part: user-space development. My day covered the topics of: Embedded Linux development introduction, how to build, autobuilding, how to run, git basics, debugging, profiling and finally some brief words on testing. A few weeks ago I decided to give Chrome a good ride on my main machine, a Debian Linux unstable. I use it a lot, every day, and I of course use my browser during a large portion of my time in front of it. I’m a long time Firefox fan and when I’ve heard and read other people converting I’ve always thought it’d be hard for me due to my heavy use of certain plugins, old habits and so on.
A few weeks ago I decided to give Chrome a good ride on my main machine, a Debian Linux unstable. I use it a lot, every day, and I of course use my browser during a large portion of my time in front of it. I’m a long time Firefox fan and when I’ve heard and read other people converting I’ve always thought it’d be hard for me due to my heavy use of certain plugins, old habits and so on. ts own URL and its own password. But Firefox just cannot remember them separately!!! These are pages I visit several times each day to ack or reject posts etc. Chrome remembers the passwords excellently for all the individual lists. This makes me a much happier person.
ts own URL and its own password. But Firefox just cannot remember them separately!!! These are pages I visit several times each day to ack or reject posts etc. Chrome remembers the passwords excellently for all the individual lists. This makes me a much happier person.